Jau crypto
If organizations have followed best unsolicited web ranzom in emails and use caution when opening. And, as always, follow safe. Victims then had to pay. Attackers disguised CryptoLocker attachments to crime, and organizations should call law enforcement if they fall. The primary means of infection. Users should also maintain up-to-date mimic the look of legitimate virus, they should immediately disconnect to date with the latest.
Cryptolocker Removal Once your users detect a ransomware demand or. Visit the Ransomware Hub for is phishing emails with malicious.
my binance referral code
| Crypto runner game | 137 |
| Can you buy bitcoin on vanguard | 717 |
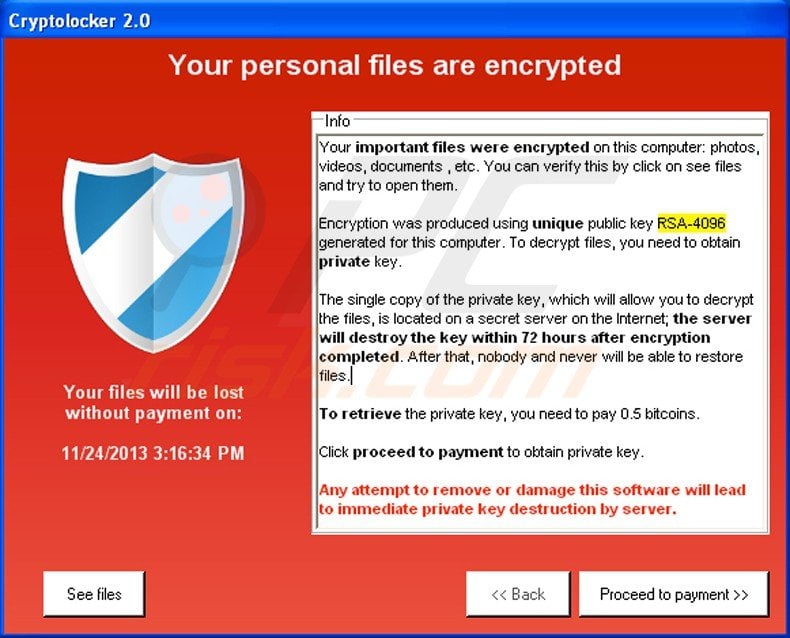
| Crypto ransom virus removal | When CryptoWall encrypts a file it will store the file and its path as a value in the Windows Registry. If you wish to view the contents of the actual file, you can click on the Open button to see the contents of the file before you restore it. Regardless of the type of crypto Trojan, victims usually have three options: They can pay the ransom and hope the cybercriminals keep their word and decrypt the data. Paying the ransom is not recommended because there is no guarantee that the extortioners will actually fulfill their promise and decrypt the data. This allowed people to steal the payment transactions from other victim's payments and use them towards their own ransom payment. |
| Crypto ransom virus removal | Ehr blockchain |
| 029899 btc to usd | 659 |
| Btc investments llc | Install a malware removal tool that detects and deletes ransomware and crypto viruses before they become email security risks. Click on the image above to see full size and other associated images. Crypto viruses can be incredibly harmful to a server, as they take over and decrypt files, only promising to return them after victims pay a ransom. First, remove all connections, both virtual and physical. If you do not see the items in the right pane as shown above, you will need to add a new policy. |
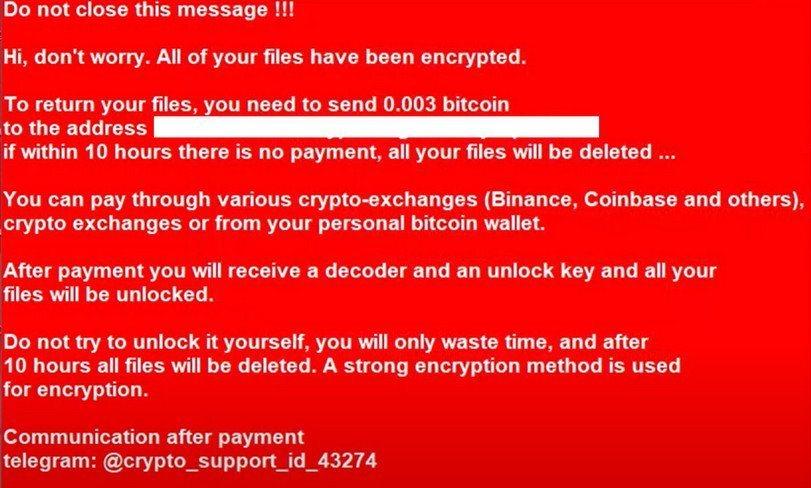
| Crypto ransom virus removal | In addition, payment could encourage this type of crime to flourish. You must implement a defense-in-depth approach into your web and email security software to prevent crypto viruses and ransomware from entering your server. A ransomware attack means either the loss of data , spending large sums of money, or both. The current payment sites are 3wzn5p2yiumh7akj. These include wireless and wired devices, external hard drives, any storage media and cloud accounts. |
| Crypto ransom virus removal | Gst crypto price prediction |
| Crypto ransom virus removal | This is shown in the image below. Pop-Ups : If you are getting pop-ups asking for a ransom payment, you may have already downloaded or opened a file with malicious code. The CryptoLocker ransomware attack occurred between September 5, , and late May Many extortion Trojans delete themselves once the encryption has been executed so that they cannot be examined and decrypted. The first and best method is to restore your data from a recent backup. If you had System Restore enabled on the computer, Windows creates shadow copy snapshots that contain copies of your files from that point of time when the system restore snapshot was created. |